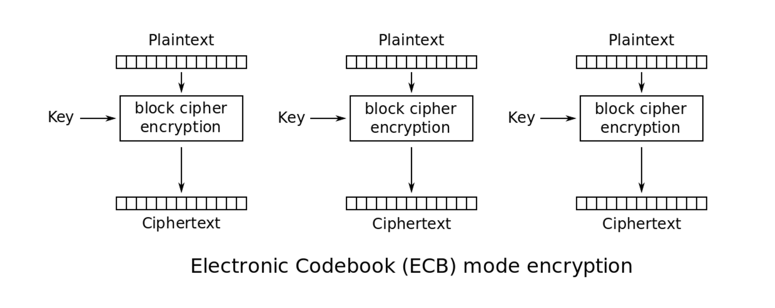
key generation - How exactly is the output of the XOR step in PBKDF2 used? - Cryptography Stack Exchange

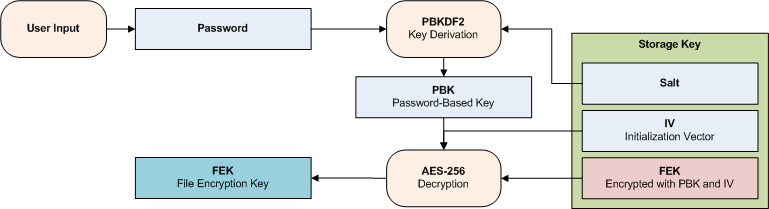
java - Encryption and Decryption with PBKDF2 and AES256 - practical example needed - how do I get the Derived key - Stack Overflow

key generation - How exactly is the output of the XOR step in PBKDF2 used? - Cryptography Stack Exchange
GitHub - sfstpala/python3-pbkdf2: Python 3 implementation of PBKDF2 (Password based key-derivation function from rfc2898)

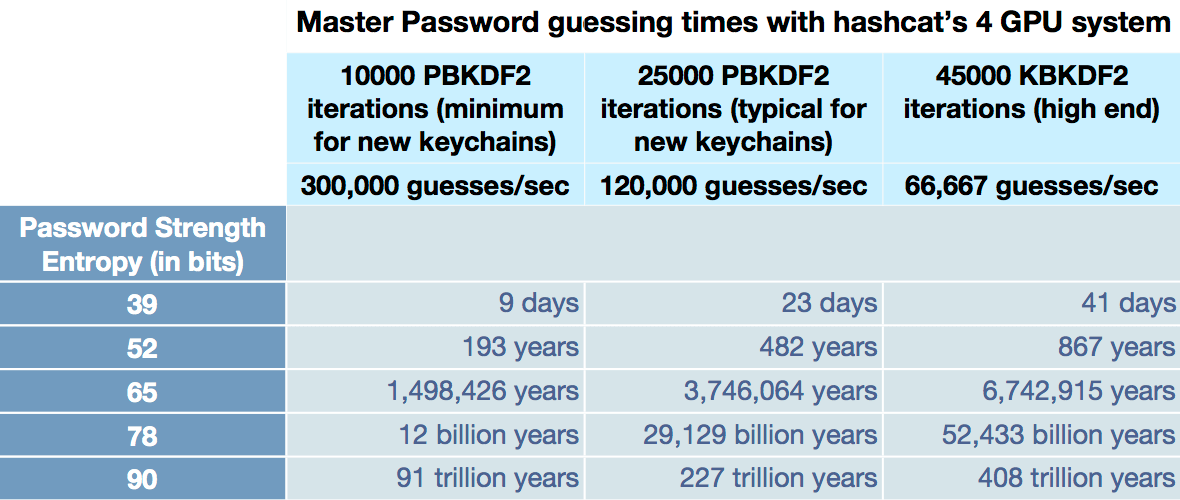
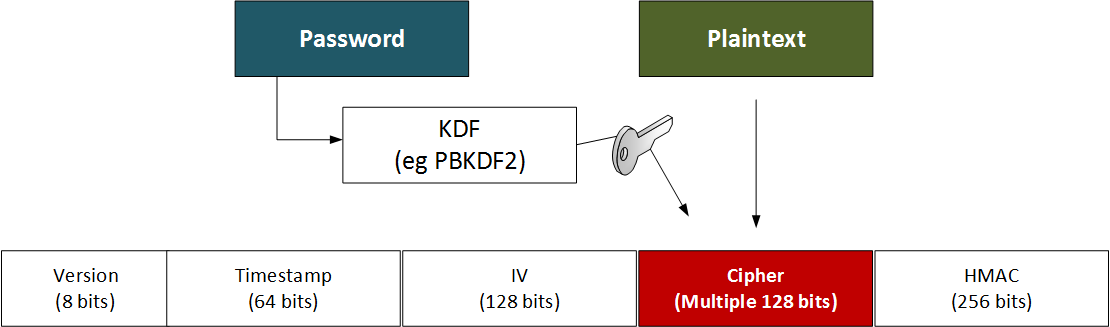
key derivation - Is a PBKDF2-derived master key easier cracked if very many Data Protection Keys are derived from it? - Cryptography Stack Exchange